Key findings
- Internet filtering technology developed by Netsweeper, Inc. has been identified on the networks of nine Bahrain-based ISPs.
- Testing on the ISP Batelco shows that at least one of the Netsweeper installations is being used to filter political content, including content relating to human rights, oppositional political websites, Shiite websites, local and regional news sources, and content critical of religion.
- These installations appear to have become active between May and July 2016, a few months after the release of a public tender by Bahrain’s Telecommunications Regulatory Authority in January 2016 indicating Netsweeper won a bid to provide a ‘national website filtering solution.’
- Our testing suggests that Netsweeper installations in Bahrain are communicating with and receiving updates from Netsweeper Inc.-controlled infrastructure.
- Bahrain has been in a period of extended political crisis since a stifled uprising in 2011, and the Bahraini government has engaged in a series of repressive tactics against oppositional political figures and human rights activists, including torture, arbitrary arrests and the revocation of oppositional figures’ citizenship.
- The sale of technology used to censor political speech and other forms of legitimate expression, to a state with a highly problematic human rights record, raises serious questions about the corporate social responsibility practices of Netsweeper, Inc.
Introduction
In January 2016, a public tender appeared on the website of the Bahrain Tender Board that indicated Netsweeper, Inc. had successfully won a bid to provide a ‘National website filtering solution’ for the country. Bahrain has a long track record of censoring critical political speech and opposition voices, both online and off, and the country has been implicated in a broad range of human rights violations, from arbitrary arrests to torture to violent crackdowns on peaceful demonstrations. The sale of filtering technology by a Canadian company to Bahrain, used to block access to information and restrict freedom of speech, thus raises important questions of corporate social responsibility. The sale comes at an interesting time: Canada has in recent months sought to expand ties with the Gulf Cooperation Council (GCC), a regional intergovernmental partnership involving Bahrain, Kuwait, Oman, Qatar, Saudi Arabia and the UAE. In May 2016, Canada’s Minister of Foreign Affairs met with GCC representatives, and “looked forward to expanded GCC-Canada relations”, including “further cooperation in the social, economic, educational, cultural and scientific fields, and human rights.”
We set out to investigate the presence of Netsweeper installations in Bahrain using a variety of network measurement techniques to identify filtering and the presence of middleboxes for implementing filtering. Part 1 of this report describes prior research on the use of Netsweeper technology in countries with questionable human rights records, and describes the current political and legal context in Bahrain. Part 2 of this report describes the results of our technical research on the use of Netsweeper technology in Bahrain.
This report is part of our ongoing research to gather empirical evidence on the use of Internet filtering technology in national jurisdictions, like Bahrain, where human rights are routinely violated with impunity. To date, very few Internet filtering companies acknowledge the human rights offending implications of their sales and services, and Netsweeper in particular appears to have no public-facing policies or statements on these issues. The aim of this research report is to confirm the presence of Netsweeper’s technology in Bahrain using network measurement techniques, describe how the technology functions and is configured within the country, and then test for access to a range of content that may be targeted for filtering.
On September 8, 2016, we sent a letter to Netsweeper, Inc. with questions regarding its provision of technology and services to Bahrain and its associated human rights due diligence. We committed to publishing the company’s response in full alongside this report. We have published a copy of the letter here. As of September 20, 2016, we have not received a reply.
Part 1: Background
Prior Citizen Lab Research on Netsweeper
Netsweeper, Inc. is a privately-owned technology company based in Waterloo, Ontario, Canada, whose primary offering is an Internet content filtering product and service. The company has customers ranging from educational institutions and corporations to national-level Internet Service Providers (ISPs) and telecommunications companies. Internet filtering is widely used on institutional networks, such as schools and libraries, and networks of private companies, to restrict access to a wide range of content. However, when such filtering tools are used to implement state-mandated Internet filtering at the national level, questions around human rights — specifically access to information and freedom of expression — are implicated.
Citizen Lab has developed a methodology for identifying installations of filtering products operating on large public ISPs. Using a combination of network scanning and in-network testing, we are able to confirm the use of these filtering products and enumerate what types content are being blocked. In doing so, questions frequently arise regarding the corporate social responsibility practices of the companies developing this technology.
Prior research by the OpenNet Initiative (2003-2013), of which Citizen Lab was a part, identified the existence of Netsweeper’s filtering technology on ISPs operating in the Middle East, including Qatar, United Arab Emirates (UAE), Yemen, and Kuwait. We outlined evidence of Netsweeper’s products on the networks of Pakistan’s leading ISP, Pakistan Telecommunication Company Limited (PTCL), in a report published in 2013, and discussed their use to block the websites of independent media, and content on religion and human rights. We have also reported that Netsweeper products were being used by three ISPs based in Somalia, and raised questions about the human rights implications of selling filtering technology in a failed state. In a report on information controls in Yemen in 2015, we examined the use of Netsweeper technology to filter critical political content, independent media websites, and all URLs belonging to the Israeli (.il) top-level domain.
Included in some of these reports were letters with questions that we sent to Netsweeper, which also offered to publish any response from the company in full. Aside from a defamation claim filed in January 2016, and then subsequently discontinued in its entirety on April 25, 2016, Netsweeper has not responded to us.
Background on Bahrain
Political context
The Kingdom of Bahrain is an island monarchy situated off the east coast of Saudi Arabia. Bahrain’s King is the head of government, and is tasked by the 2002 Constitution with appointing ministers, judges, and half of the legislature. As part of the Arab Spring in 2011, protesters in Bahrain took to the streets, demanding democratic political reform, an end to corruption and discrimination against the Shia sect, and the removal of Bahrain’s long-serving Prime Minister. Protests snowballed as security forces killed protesters, and culminated in protesters’ occupation of the Pearl Roundabout, a traffic junction in Bahrain’s capital city, for one month. In March 2011, troops from Saudi Arabia and the United Arab Emirates entered Bahrain, and security forces forcibly cleared and demolished the Pearl Roundabout. Three months later, Bahrain’s King established the Bahrain Independent Commission of Inquiry (BICI), which concluded that police and security forces engaged in “grave violations of human rights, including the arbitrary deprivation of life, torture and arbitrary detention.”
Human Rights Watch and Amnesty International continue to criticize the government of Bahrain for perpetrating human rights violations, including arresting those who criticize the government, stripping dissidents of their citizenship on the grounds of national security, and routinely maltreating and torturing prisoners. In 2014, the 1963 Bahraini Citizenship Act was amended to grant the Interior Ministry additional authority to revoke a Bahraini national’s citizenship if he or she has failed in their “duty of loyalty” to the state. Human Rights Watch argued against this vaguely worded provision, fearing that it could be used against government critics. Advocacy groups have also appealed to the international community to put pressure on the Kingdom. In a letter read to the UN Human Rights Council in September 2015, a group of 32 countries, including United States and the United Kingdom, urged Bahrain to take steps to better protect the fundamental human rights of its citizens.
Since the 2011 uprising, numerous social media users and bloggers have been targeted by authorities as a result of their online activities. Bahrain Watch has compiled a list of individuals arrested as a result of their online activities, which includes individuals imprisoned and tortured for allegedly insulting the King online and inciting anti-government hatred. In some cases citizenship was revoked.
Crackdown on opposition voices continued in 2016. In June, Nabeel Rajab, the founder of the Bahrain Centre for Human Rights, was arrested for “spreading false information and rumours with the aim of discrediting the State,” a move which was widely condemned by human rights observers. The Kingdom was also criticized for placing Rajab in solitary confinement. This was not the first time that Rajab was targeted. He was arrested in April 2015 following a series of tweets condemning torture and Bahraini involvement in the ongoing conflict in Yemen, and in October 2014 for tweets calling the Ministry of Interior an “ideological incubator” for ISIS after several officers defected to ISIS, and in July 2012 after criticizing the Prime Minister on Twitter.
In June 2016, a Bahraini court ordered the shutdown of Al Wefaq, the country’s largest opposition group. The court found that the group “repeatedly objected [to] the legitimacy of Bahrain’s constitution, supported violent action and posted pictures of terrorists brandishing sharp tools while claiming they were peaceful demonstrators.” The ban came a week after an appeals court extended the prison sentence of Sheikh Ali Salman, the political leader of Al Wefaq, from 4 to 9 years. He was found guilty in 2015 on charges which included “promoting political change using illegal forceful means and threats”. Shortly afterwards, the Ministry of Interior revoked the citizenship of leading cleric Sheikh Isa Qassim for allegedly serving “foreign interests” and escalating sectarian divisions in the country. Qassim, considered the “spiritual voice” of Bahrain’s Shia community, has been a vocal critic of the government’s repressive crackdown in recent years. The incident marked the 300th citizenship revocation in Bahrain since 2014, and was condemned by both the office of the UN High Commissioner for Human Rights and the US State Department. Demonstrations in Qassim’s home of Duraz following the citizenship revocation were met with a strong police presence, and Internet disruptions.
In August 2016, United Nations independent human rights experts urged Bahrain to end harassment of the Shia population in Bahrain, saying “Shias are clearly being targeted on the basis of their religion.” The experts stated: “Recently, we witnessed the dissolution of Al-Wefaq National Islamic Society, the shutting of faith-based organizations, restrictions on the practice of religious rites, on Friday prayers and peaceful assemblies, restrictions on movement, restricted access to the Internet and a ban on Shia religious leaders from preaching.” It is worth noting that Bahraini government officials and parliament members have denied accusations made by advocacy groups. For example, a legislator and member of Bahrain’s Board of Commissioners of the National Institution for Human Rights denounced the August 2016 United Nations human rights experts’ statement as baseless allegations and a “sectarian-tinted statement” containing “false information and fallacies.”
Information Controls
Bahrain is rated by Freedom House’s 2015 Freedom on the Net report as ‘Not Free’, earning it the 9th lowest score of the 65 countries examined. The country was named by Reporters Without Borders as one of the ‘Enemies of the Internet’. Information controls in the country take a number of forms, including widespread censorship and surveillance, strict press laws prohibiting the online activities of the press, government use of PR companies to shape the media narrative, and the targeting and imprisonment of users for their online activities.
Internet Censorship and Shutdowns
Bahrain is one of the most wired countries in the Middle East, but it is also one that has an established track record of censoring Internet communications. The OpenNet Initiative has documented the extent of censorship in the country for a decade. Testing conducted in 2006 on the ISP Batelco found that sites critical of the Bahraini government and monarchy, LGBT content, anonymization tools, and religious conversion sites were all blocked. Tests run in 2009 found filtering to be more extensive than in prior tests, with domestic political criticism and human rights organizations found censored, along with an increase in the blocking of pornographic and LGBT content. In 2011, blocking in Bahrain was found to be implemented through the use of McAfee’s SmartFilter product.
Numerous government ministries and organizations have a role in Bahrain’s online information controls. The Telecommunications Regulatory Authority (TRA), established in 2002, is the primary regulatory body for the country. The Information Affairs Authority (IAA), established in 2010, operates the country’s official media outlets and is responsible for issuing censorship orders for both online and offline media. The IAA requires the registration of all websites, and blocks websites found to be in violation of Articles 19 and 20 of the 2002 Press Rules and Regulations, which state:
Article 19
As per a decision by the minister, it is possible to prohibit circulation of publications instigating hatred of the political regime, encroaching on the state’s official religion, breaching ethics, encroaching on religions and jeopardizing public peace or raising issues whose publication is prohibited by the provisions of this law.
Concerned parties can appeal the decision to prohibit circulation before the High Civil Court within 15 days of its issuance or notification. The court shall settle the case on an urgent basis.
Article 20
As per a decision by the minister, it is possible to bar any publication issued abroad from entering and circulating in the kingdom so as to maintain public order, morals, religions or due to any other reasons related to the public interest.
Concerned parties can appeal the decision of prohibition before the High Civil Court within 15 days of its issuance or notification and the court shall settle the case on an urgent basis.
In July 2016, the Bahrain Information Minister issued Decree 68/2016, which required media outlets to obtain licenses from the Mass Media Directorate in order to publish news online, limited video or audio clips to two minutes in length, and prohibited live-streaming. The decree was criticized as further restricting Bahrain’s already strict press censorship, with provisions requiring licensees to provide individual names, websites and social media account information, seen as a method of facilitating easier punishment of individuals for publishing controversial material.
In August 2016, the TRA issued Decision 12/2016, requiring that all telecommunications companies in Bahrain purchase and use a “unified technical system” for blocking websites. We discuss this requirement in connection to our research on Netsweeper in more detail below.
Research published by Bahrain Watch in August 2016 documented the nightly disruption of mobile and fixed-line services offered by providers Batelco and Zain in the Duraz region that had been taking place since June 23. According to Bahrain Watch, “Duraz has been the focal point of ongoing protests since 20 June 2016, when the government revoked the citizenship of [Shia religious leader] Sheikh Isa Qassim,” a resident of Duraz. In late August 2016, a coalition of organizations concerned with Internet shutdowns wrote a letter to the TRA, requesting authorities cancel service restriction orders issued for Duraz, in accordance with a June 2016 UN Human Rights Council resolution that condemned “measures to intentionally prevent or disrupt access to or dissemination of information online in violation of international human rights law” and called on states to “refrain from and cease such measures.” Notably, the Duraz disruptions are not the first instance of connectivity restrictions in Bahrain as a result of protest; Arbor Networks documented a significant drop in traffic during the 2011 uprising.
Surveillance
In 2012, Citizen Lab published a report describing the use of surveillance malware FinFisher to target Bahraini activists, a claim which was denied by a Bahrain government spokesperson. Following the 2014 breach of FinFisher developer Gamma International’s networks, leaked documents showed that the malware had been used to compromise the computers of potentially dozens of human rights lawyers, politicians and exiled activists. In 2014, leaked documents from spyware company Hacking Team showed that the Bahrain Ministry of Interior purchased that company’s Remote Control System software, and that a legal review Hacking Team commissioned to investigate the sale of surveillance tools to Bahrain noted the ongoing human rights concerns in the country.
Bahrain has jailed dozens of netizens for expressing critical opinions online, including those using pseudonymous accounts. In some cases, those arrested appear to have been identified using “IP Spy” links sent by the government. When a target clicks on such a link, their IP address is logged and sent to the government, who then sends a request to the user’s ISP to get the associated subscriber’s name and address.
Facebook was widely used to organize during the 2011 uprising; however, reports have suggested that Facebook groups were also used to monitor and identify protesters — in one case reportedly leading to the arrest and torture of prominent anti-government protester Ayat Al Qurmezi.
Part 2: Netsweeper in Bahrain
In January 2016, the Bahraini government’s online tender website displayed a Telecommunications Regulatory Authority tender for a ‘National Website Filtering Solution,’ which appeared to have been won by Netsweeper for either $1.1M USD or $3.1M USD. Netsweeper appears to have been the only bidder, as the document says the number of bids submitted was only one. The tender type was listed as “selected,” indicating that the government invited a small number of companies to bid on the tender. Netsweeper did not respond to media inquiries about this tender.
With the release of the TRA tender appearing to indicate Netsweeper, Inc. had been chosen to deploy a ‘National website filtering solution’, we set out to investigate the presence of Netsweeper technology on networks in Bahrain.
This research set out to answer three basic questions:
- Are Netsweeper installations present on the networks of Bahrain-based ISPs?
- If so, are these installations used to filter content? In particular, are they used to filter critical political content or speech otherwise protected by international human rights law?
- If Netsweeper installations are present in Bahrain, are they communicating with Netsweeper, Inc.-controlled infrastructure? For example, are they receiving updates to categorization databases?
Answering each of these questions required a range of methods, including:
- Network scanning data to determine the presence of devices that match Netsweeper fingerprints;
- In-country and proxy testing to identify filtering behaviour at the ISP level; and
- The use of a ‘beacon box’ or ‘phone home’ test to determine if Netsweeper installations in Bahrain are communicating with Netsweeper, Inc.-controlled infrastructure.
In the following section, we will describe the results of our research to answer these three questions.
Technical analysis
In this section we will explore and try to resolve the three questions posed about the presence and function of Netsweeper installations in Bahrain.
1. Are there Netsweeper devices in Bahrain?
To identify the presence of Netsweeper technology on Bahrain-based ISPs, we queried two services that aggregate Internet-wide scanning data: Censys and Shodan. We used Censys to look for visible HTTP interfaces of Netsweeper products, and we used Shodan to find SNMP1 interfaces. We used a range of different queries to find different instances of Netsweeper installations. The queries were based on both prior research and trial and error experimentation. The full list of queries used for finding these installations are outlined below:
| Provider | Query | Details |
|---|---|---|
| censys | 80.http.get.title: “Netsweeper Business” | HTTP interface of Business branded Netsweeper installations. |
| censys | 80.http.get.title: “Netsweeper SMB” | HTTP interface of Business branded Netsweeper installations. |
| censys | 80.http.get.title: “Netsweeper School” | HTTP interface of Education branded Netsweeper installations. |
| censys | 80.http.get.title: “Netsweeper Cloud Manager” | HTTP interface of generic branded Netsweeper installations. |
| censys | \/webadmin\/common\/templates\/ | A common code element in Netsweeper HTTP interfaces. |
| censys | \/webadmin\/deny\/index.php | Default url path for Netsweeper block pages |
| shodan | .el5.netsw | Common SNMP sysDescr value for Netsweeper installations. |
| shodan | .el6.netsw | Common SNMP sysDescr value for Netsweeper installations. |
Table 1 – Queries used in preliminary identification of Netsweeper devices.
We restricted our queries to IP addresses geo-located in Bahrain.2
We then visited the IP addresses directly and captured the results to verify they were running the Netsweeper web administrator interface as seen in Figure 1.
Accessing the path of “webadmin/deny/index.php” on the visited IPs will show the configured deny page as shown in Figure 2.
Table 2 lists every IP address where we found Netsweeper web interfaces to which we were able to connect. In one instance, we identified an IP address (188.137.140.21) using Shodan with the hostname “netsweeper-02.i.infonas.com”, on the network of Infonas (formerly 2Connect)3 but as we were unable to connect to the web interface it has been excluded from the table.
| IP Address | AS Name |
|---|---|
| 62.209.25.186 | MTC Vodafone Bahrain (B.S.C.) |
| 109.161.148.250 | MTC Vodafone Bahrain (B.S.C.) |
| 80.241.146.26 | Northstar Technology Company W.L.L. |
| 80.95.222.114 | Etisalcom Bahrain Company W.L.L. |
| 80.95.222.115 | Etisalcom Bahrain Company W.L.L. |
| 84.235.107.71 | VIVA Bahrain BSC Closed |
| 84.235.107.72 | VIVA Bahrain BSC Closed |
| 84.235.107.203 | VIVA Bahrain BSC Closed |
| 84.235.107.206 | VIVA Bahrain BSC Closed |
| 87.236.136.186 | Nuetel Communications S.P.C |
| 87.236.136.187 | Nuetel Communications S.P.C |
| 87.236.52.38 | Kalaam Telecom Bahrain B.S.C. |
| 185.34.229.236 | Rapid Telecommunications W.L.L. |
| 185.34.229.237 | Rapid Telecommunications W.L.L. |
| 193.188.97.224 | Batelco |
Since Netsweeper devices were spread across ISPs in Bahrain we examined the associated block pages to see if there was any overlap in regards to which networks they are on. The blockpage of www.anonymous.com.bh was reported as early as 2009 in Bahrain.
Using the text on that block page we made a query to see what other sites in Bahrain have similar text. This search lead us to three additional IP addresses with block pages that contained similar text and design elements to the anonymous.com.bh blockpage.
| IP Address | AS Name | Hostname (if any) |
|---|---|---|
| 83.136.59.52 | MTC Vodafone Bahrain (B.S.C.) | |
| 83.136.58.185 | MTC Vodafone Bahrain (B.S.C.) | block.bb.zain.com |
| 193.188.112.86 | Batelco | www.anonymous.com.bh |
| 188.137.140.22 | Infonas WLL |
Table 3: Blockpages in Bahrain and their associated AS Name.
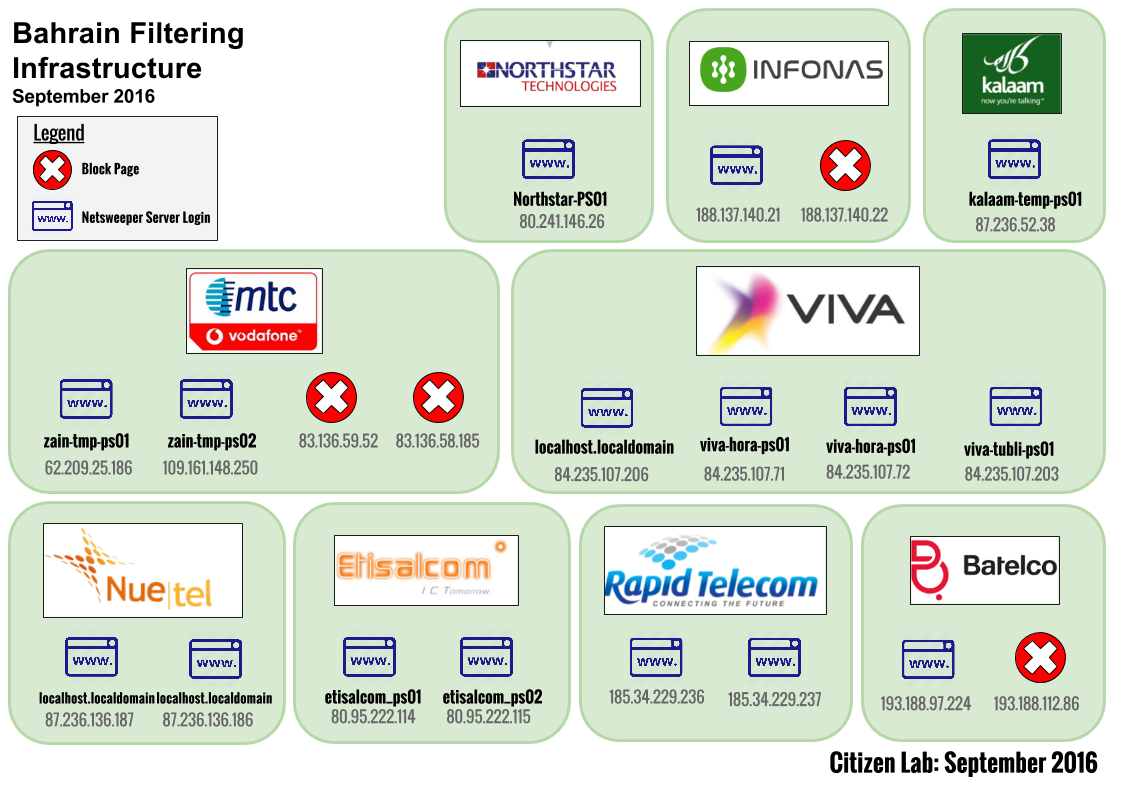
Clustering the Netsweeper IP addresses along with the blockpage reveals overlap as shown in Figure 4. MTC-Vodafone has two Netsweeper servers as well as two blockpages. Batelco and Infonas each have a single Netsweeper server and a single block page on their network. The rest of the ISPs only have Netsweeper servers, ranging from one to four per ISP.
We also attempted to retrieve the SNMP ‘sysName’ value of any Netsweeper IP addresses which have the SNMP port open and the service running. We looked at the sysName value because it is commonly used to relay the hostname of a device, and the hostname may indicate the function of the device in the context of the larger installation. We retrieved this value using snmpwalk requesting the standard OID for sysName. The SNMP information retrieved is presented in Table 4.
| IP Address | AS Name | SNMP SysName |
|---|---|---|
| 62.209.25.186 | MTC Vodafone Bahrain (B.S.C.) | zain-tmp-ps01 |
| 109.161.148.250 | MTC Vodafone Bahrain (B.S.C.) | zain-tmp-ps02 |
| 80.95.222.114 | Etisalcom Bahrain Company W.L.L. | etisalcom_ps01 |
| 80.95.222.115 | Etisalcom Bahrain Company W.L.L. | etisalcom_ps02 |
| 84.235.107.203 | VIVA Bahrain BSC Closed | viva-tubli-ps01 |
| 84.235.107.206 | VIVA Bahrain BSC Closed | localhost.localdomain |
| 84.235.107.71 | VIVA Bahrain BSC Closed | viva-hora-ps01 |
| 84.235.107.72 | VIVA Bahrain BSC Closed | viva-hora-ps01 |
| 87.236.136.186 | Nuetel Communications S.P.C | localhost.localdomain |
| 87.236.136.187 | Nuetel Communications S.P.C | localhost.localdomain |
| 185.34.229.236 | Rapid Telecommunications W.L.L. | rapid-ps01 |
| 185.34.229.237 | Rapid Telecommunications W.L.L. | rapid-ps02 |
| 80.241.146.26 | Northstar Technology Company W.L.L. | Northstar-PS01 |
| 87.236.52.38 | Kalaam Telecom Bahrain B.S.C. | kalaam-temp-ps01 |
Table 4: SNMP SysName values for Netsweeper servers in Bahraini ISPs.
In most cases, the SNMP sysName is the name of the ISP followed by ‘PS’ and a number. ‘PS’ likely refers to the Netsweeper policy server, which is the name of the component of a Netsweeper installation that performs the blocking logic. Both Zain and Kalaam Telecom’s sysNames refer to their installations with the word temp, implying that these may be temporary installations.
HTTPS certificate dates
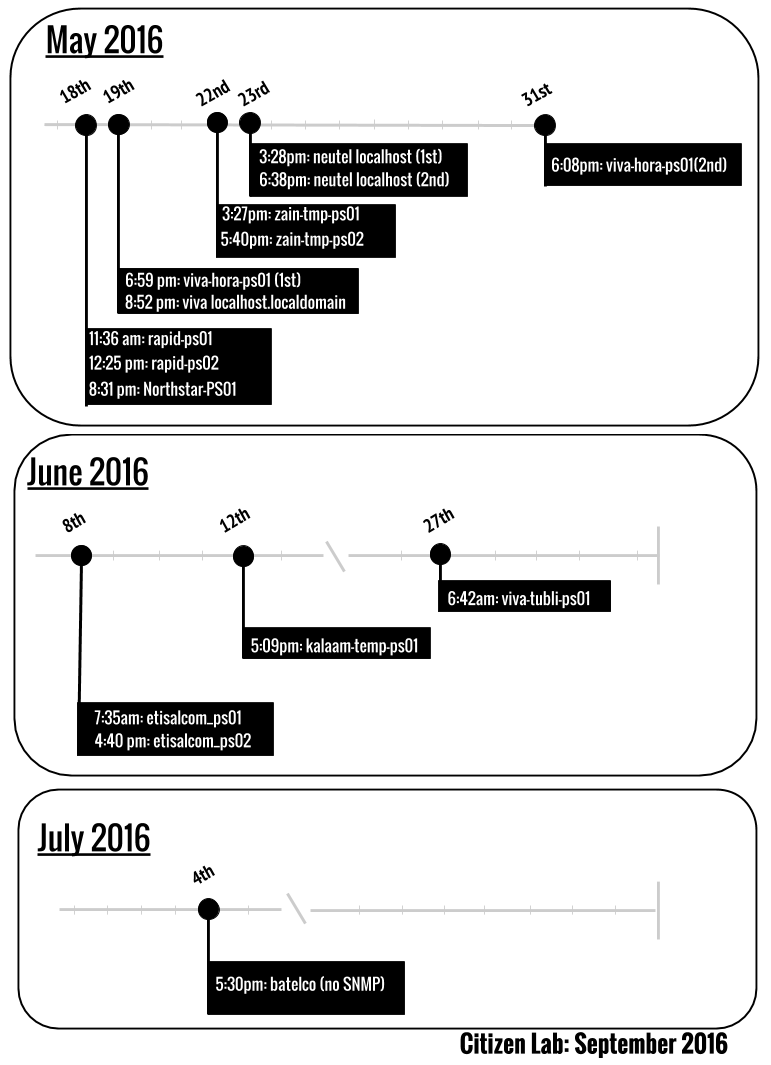
We also examined the HTTPS certificates present on the web interfaces of the Netsweeper login pages. These are relevant because they can help estimate the date and time the local Netsweeper server was configured on the network of the ISP. It is not standard practice for HTTPS certificates to come pre-installed by the developer (as this would provide Netsweeper, Inc. with the ISP’s private key) so it is likely that the certificates have been generated upon initial configuration at the ISP. We investigated the validity values on the certificates and focus here on the “Issued on” value, which suggests the date the server was configured. We adjust the timezone to Arabia Standard Time (AST) and present these values on a timeline in Figure 5.
We see the earliest certificate being generated May 18, 2016 at Rapid Telecom and the last at Batelco on July 4, 2016. The totality of certificates is generated in this three month span. Most of the certificates were generated during daytime hours (AST), and grouped according to ISP. For example, we see Nuetel configure the whole infrastructure we identify on May 23, 2016 within three hours. Conversely, the installation at VIVA is the most spread out on the timeline ranging from May 19 to June 27. In total, this evidence suggests that Netsweeper installations appeared on a series of Bahraini ISPs four months after the TRA tender announcing Netsweeper’s bid on the filtering system.
2. Are Netsweeper devices filtering content in Bahrain?
Netsweeper blocking fingerprint
Although our network scanning data confirms the presence of Netsweeper installations on the networks of Bahraini ISPs, it alone does not tell us whether the installations are actively being used to filter content for customers of these ISPs. In order to test whether the installations were used to filter content, we attempted to access censored content on the ISP Batelco and examined the responses.
We accessed the website of the Arab Times (arabtimes.com), which has been identified as being blocked, using a public proxy on the Batelco network. When we accessed this page we received the following response:
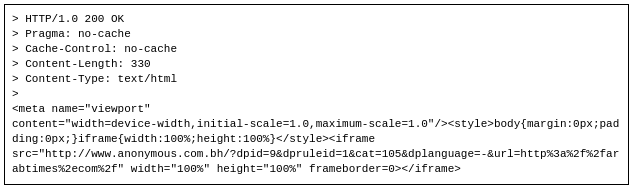
The response contains an iframe to www.anonymous.com.bh, the blockpage we have identified as being in use since 2009 in Bahrain. An interesting addition in this response is the parameters after the “/” sent to this block page URL. We URL decode and add newlines to the parameters to increase legibility of this here:
These values: dpid, dpruleid, cat and dplanguage are identical parameters used by Netsweeper installations we have seen in Pakistan, Somalia, and Yemen. The cat parameter denotes the categorization of the blocked URL. The current mapping of category number to readable name is available here. Category number 105 refers to the “Custom” category, or a URL that was manually entered by the ISP administrators.
The packet capture collected from this Batelco vantage point also showed that our computer received two different responses: one with the blockpage in an iframe as seen above, and a response containing the legitimate Arab Times front page shortly thereafter. This behavior is consistent with packet injection from a device located between the user and website. If a requester receives the blockpage response first, it will render the blockpage and discard the second, legitimate, response. The injected blockpage response has a Time-To-Live (TTL) value of 61. Assuming that the initial TTL is set to 64 (a common value for initial TTLs), this indicates that the device performing the injection is close to the user. As a result, the injecting server will almost always win the race versus the legitimate response, guaranteeing that most web browsers will only show the block page response. This process renders the legitimate content inaccessible.
In addition, all injected responses also have an identical IPID value of 242. An IPID is a value set in the IP header of a packet that is used primarily for reassembly and fragmentation of data exchanges. This value can be set differently by the operating system that sent the packet; some will set it to zero, others will set it to the same number, and others might just increment the value with each packet sent. This IPID value is particularly relevant here, as our research showed that Netsweeper devices in Yemen also used an IPID value of 242.
Content types found blocked
To confirm that Netsweeper products were being used to censor content on Bahrain-based ISPs, as well as to identify the types of content that were being blocked, we conducted manual testing from a vantage point on the ISP Batelco.
These limited tests consisted of connecting to a proxy on the Batelco network, and attempting to access a list of sensitive Bahrain-specific and regional content in a web browser. All URLs that generated a blockpage were identified as blocked. (The absence of a given URL from the list of blocked URLs does not definitively indicate that the URL is accessible on Batelco) A full list of URLs tested and those found blocked can be found in the Data section at the end of this report. In-country testing was limited out of concern for tester security. Further research is required to identify filtering behaviour on additional ISPs in Bahrain.
The types of content found blocked via this method of testing include:
| Content type | Examples |
|---|---|
| Websites affiliated with local political groups including the opposition movements al-Wefaq, Bahrain Freedom Movement and February 14 | http://alwefaq.net
http://www.14febrayer.com |
| Websites of local human rights and advocacy organizations | http://www.bahrainrights.org |
| Bahraini publications that post content critical of the government of Bahrain | http://bahrainmirror.com
http://bahrainalyoum.net http://lualuatv.com http://alduraz.net |
| Websites on the Shia sect | http://shiaweb.org
http://albrhan.org http://www.ansarh.com |
| Websites which have content critical of Islam | http://answering-islam.org
http://www.faithfreedom.org |
| Atheism content in Arabic | http://arabel7ad.blogspot.com
http://www.ladeeni.net |
| Iranian media outlets | http://www.alalam.ir |
| Media affiliated with Lebanon’s Hezbollah | http://www.almanar.com.lb |
| Regional Arabic news websites | http://www.alquds.co.uk |
| Regional human rights and free speech advocates | http://www.anhri.net |
| Gambling websites | http://www.cdl.com.lb
http://www.williamhill.com |
| Anonymization and circumvention tools | http://www.xroxy.com
http://www.samair.ru http://www.proxyfire.net http://anonym.to |
| Arab Christian websites | http://www.arabchurch.com |
| Arabic secular discourse | http://www.rezgar.com |
| All content categorized by Netsweeper as ‘Pornography’, ‘Gambling’, ‘Viruses’, or ‘Web Proxy’ | See ‘Deny Page Tests’ section below:
http://denypagetests.netsweeper.com/category/catno/10 http://denypagetests.netsweeper.com/category/catno/21 http://denypagetests.netsweeper.com/category/catno/23 http://denypagetests.netsweeper.com/category/catno/32 |
Table 5: Examples of URLs found blocked on Batelco
‘Deny page tests’
Amongst the websites tested for accessibility were a special set of URLs referred to as ‘deny page test’ URLs. These are URLs created by Netsweeper, Inc. specifically for the purpose of testing which content categories are blocked by a Netsweeper installation. A custom URL is created for each category (e.g. “pornography”, “sex education”) and that URL — while not containing any of that type of content — is categorized by Netsweeper as belonging to that category. As described by Netsweeper, Inc.:
“For example, http://denypagetests.netsweeper.com/category/catno/23, is categorized as the Pornography. When checking the Pornography category, this test will make a request to the URI of http://denypagetests.netsweeper.com/category/catno/23. If this is blocked or redirected to another page, we consider the Pornography category blocked.”
We tested 67 of the deny page test URLs from a Batelco proxy, and found the following four to be blocked:
| URL | Associated Netsweeper Category |
|---|---|
| http://denypagetests.netsweeper.com/category/catno/10 | Gambling |
| http://denypagetests.netsweeper.com/category/catno/21 | Viruses |
| http://denypagetests.netsweeper.com/category/catno/23 | Pornography |
| http://denypagetests.netsweeper.com/category/catno/32 | Web Proxy |
Table 6: ‘Deny page test’ URLs found blocked on Batelco
The blocking of these URLs is a strong indication that Netsweeper technology is being used to filter content on Batelco; we do not know of any reason these URLs would be blocked otherwise. Further, the ‘deny page test’ content categories found to be blocked are consistent with some of the types of content found blocked via proxy testing on Batelco.
It should also be noted that blocking content with a Netsweeper installation is not limited to the use of predefined content categories. System administrators are able to create ‘custom’ lists of content, including the use of wildcards, in order to block lists of content outside of the Netsweeper, Inc.-created lists. This feature is why we see content (such as human rights and news websites) blocked which do not belong to the four categories identified as blocked through the ‘deny page tests’ URLs.
3. Are Netsweeper devices in Bahrain communicating with Netsweeper, Inc.-controlled infrastructure?
Once we identified the presence of Netsweeper installations on Bahrain-based ISPs, we set out to determine if the Bahrain-based installations were communicating with any infrastructure controlled by Netsweeper, Inc. We conducted a test that used the structure of Netsweeper’s categorization system to determine if such communications were taking place.
Beacon box test
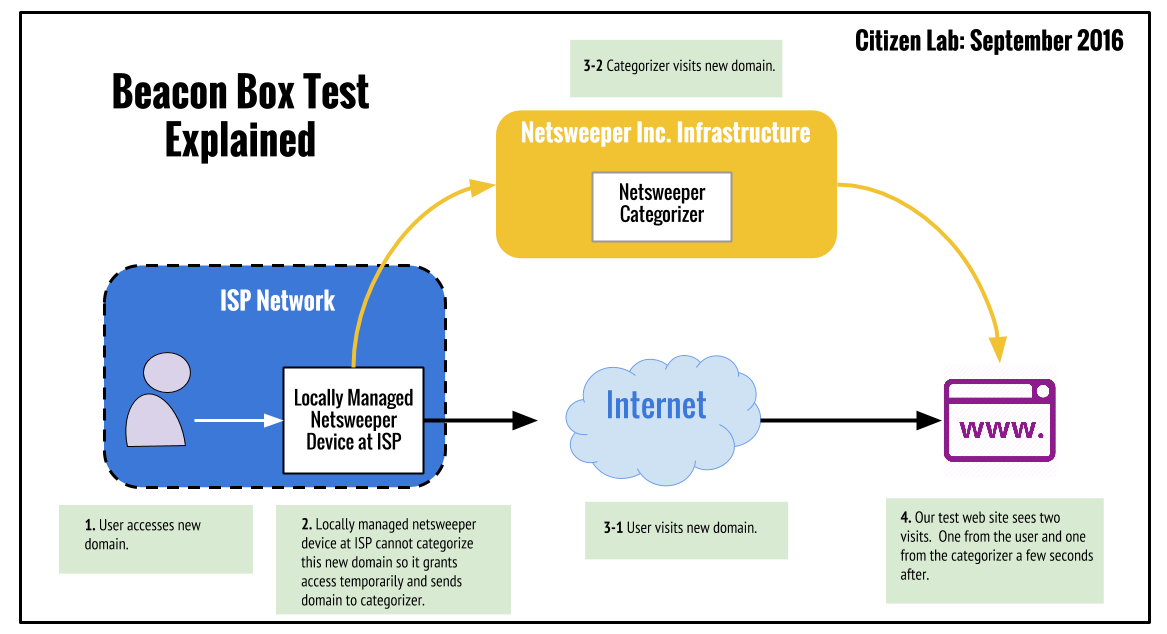
Netsweeper’s Internet filtering solution blocks content through the interaction of two systems, broadly defined: a database of website categorizations; and software that intercepts requests for websites and determines if they are to be denied or permitted. The decision on whether to deny or permit access to a given website is made by looking up the categorization of a website in the database, and then determining if that category of content has been configured to be denied or permitted, a configuration made by the Netsweeper customer.
Netsweeper, Inc., maintains the ‘master database’ of website categorizations that it hosts on its own infrastructure. A Netsweeper, Inc. customer (such as a Bahraini ISP) hosts a local copy of that database on its own networks. If a user of an ISP using Netsweeper products attempts to access a website, the Netsweeper software will look up the categorization of that website in the ‘local’ copy of the category database. Once it has determined the categorization of the website, it will either permit or deny access to that website depending on the policies configured by the ISP (or other Netsweeper customer).
However, should an individual ISP user attempt to access an uncategorized website (for example, a newly registered domain) the local Netsweeper installation will contact the Netsweeper, Inc.-controlled master category database. (In the meantime, the local Netsweeper installation will generally permit the customer to visit the website while the categorization is taking place.) This master database will run a categorization service which will access the website, perform an automated categorization of the uncategorized website’s content, add this category to the master database and then send this categorization to the ‘local’ Netsweeper installation. Netsweeper, Inc. documentation suggests that this entire process can be completed in “as little as one second and at most about a minute”.
Since we know that an attempt to access a previously uncategorized website should lead to the master category server accessing the website soon thereafter, we conducted a test to determine if a Bahrain-based Netsweeper installation is in fact communicating with Netsweeper, Inc.-controlled infrastructure. We registered a new domain and created a website with innocuous content. Since we control the servers on which this new website is hosted, we have access to the server logs and can determine who attempted to visit the website and where those requests originated from. As a result, after accessing these newly created websites from ISPs in Bahrain, we anticipated seeing a visit from the Netsweeper Master Category Server in our logs as this server attempts to dynamically categorize our website.
We have illustrated this process in Figure 6:
This test is a duplication of a similar test we performed to confirm communications between a Netsweeper installation in Yemen and Netsweeper, Inc.-controlled infrastructure. In that case, we registered six new domains and accessed three of them from YemenNet (a Netsweeper, Inc. customer) while the other three acted as a control. In all cases, the websites contained innocuous content. We found that in all three instances of the websites being accessed from YemenNet, our web servers were visited by similar IP addresses with requests containing the same user-agent string and requesting headers within one second of our accessing the website from YemenNet. This activity precisely matched a previous instance described by customers of the Australian ISP Telstra, which was later confirmed by Telstra to be Netsweeper servers performing a categorization of previously unseen websites.
We performed this test on three ISPs in Bahrain: Batelco, Zain and VIVA. We registered eight new domains: two for each of these ISPs and two to act as a control. We hosted the same identical, innocuous text content on each site, and did not access the sites beyond confirming the sites were reachable from the University of Toronto’s network. The results were as follows:
Batelco
Our server logs show both websites being requested from Bahrain. There was no evidence of any further relevant requests for either of the two websites.
VIVA
For both websites, our server logs show the original request for the website from Bahrain, which are followed roughly one second later by a request from IP addresses hosted by Digital Ocean, a large network service provider. Although each website was visited by a different Digital Ocean IP address, both requests included identical HTTP headers and user-agent strings. The user agent in this request matched the user agent seen in the Yemen experiment.
Zain
Much like the results for VIVA, our server logs show the requests for both websites from Bahrain are followed within approximately one to two seconds by a request from an IP address hosted by Digital Ocean. Again, both of the Digital Ocean IP addresses are different, however the HTTP headers and user-agent strings were identical, and the same as those seen on VIVA. This user agent again matched the user agent seen in the Yemen experiment.
Control
We did not notice any unusual visits to either of these websites, and did not identify any visits from the Digital Ocean hosted IP addresses identified in the experiment.
Beacon box test summary
The results of the tests run on VIVA and Zain are generally consistent with similar tests we ran on YemenNet, a known customer of Netsweeper. Although in that case the visits were from Rackspace-hosted IP addresses, the user-agent strings and timing of categorization visits were identical. In addition, Rackspace and Digital Ocean are companies which offer similar services, and thus it is plausible that Netsweeper, Inc. has switched providers for their categorization infrastructure. As mentioned previously, the results seen on VIVA and Zain (as well as YemenNet) are consistent with similar reports from Australian ISP Telstra which were confirmed to result from Netsweeper’s categorization process.
It is not clear why there was no evidence of the categorization service visiting the websites tested on Batelco. As network scan data and proxy testing conducted on Batelco both indicate that a Netsweeper installation is present and active, we expected our beacon box test results to show the categorization service visiting our web server. System administrators are able to configure Netsweeper installations to prevent the dynamic categorization of previously uncategorized websites, although it is not clear why a Batelco administrator would do this. We will continue tests from Batelco, where and when they are possible, to try and shed further light on this anomaly.
Summary of evidence pointing to the use of Netsweeper in Bahrain
In summary, our results indicate that Netsweeper devices are present on the networks of nine ISPs in Bahrain, that at least one of these installations is actively being used to filter content for Bahraini Internet users, and that critical political content is among the content types being filtered. The findings that support this argument are:
- Network scan data matches HTTP and SNMP fingerprints of Netsweeper installations.
- Blockpage URL parameters match those of known Netsweeper installations.
- The IPID value of injected packets matches known Netsweeper behaviour.
- HTTPS certificate ‘Issued on’ dates show installations appear across many ISPs within a short period of time, four months after Netsweeper appears to have won the TRA bid.
- The “beacon box tests” showed that two out of three ISPs tested exhibited behaviour consistent with previous instances of Netsweeper Inc.-controlled infrastructure categorizing a previously uncategorized website.
- Attempts to access the ‘deny page test’ URLs meant for testing a Netsweeper installation showed the URLs for content categories Gambling, Viruses, Pornography, and Web Proxy to be blocked on the ISP Batelco.
A unified technical system for blocking?
One unanswered question is why the TRA sought out a new filtering system. An August 2016 news article suggests that centralization may have been the motivation for purchasing a new filtering system. On August 5, 2016, the head of the TRA announced a new set of regulations stating that “all telecommunication companies in Bahrain must purchase and use a unified technical system for blocking websites”. This announcement would be consistent with the appearance of new Netsweeper installations on numerous ISPs across the country within a relatively short time span.
Further, Netsweeper’s filtering system does possess features that allow for the centralized sharing of configuration settings, called up2date. This feature allows local Netsweeper servers configured at the ISPs to pull categorizations, block lists, and deny pages from a central server. If enabled, this feature would allow a central authority such as TRA to curate the block lists, which would then be pushed out to all ISPs in the deployment.
The centralization of content filtering was a recommendation of a March 2014 study published jointly by Bahrain’s Telecommunications Regulatory Authority and Detecon, a subsidiary of T-Systems International, itself a subsidiary of Deutsche Telekom. The study recommended the creation of “a (centralized) database of blacklisted content providers — covering all categories of unsuitable/illegal content, copyright/IPR flouting, and malware distributors — for daily distribution to ISPs”. The study also notes the use of Netsweeper in Qatar, the UAE, Pakistan and Yemen, and calls for testing the feasibility of centralized content filtering within the GCC countries. Notably, the study also flags the human rights considerations of working with certain “key vendors of content filtering and blocking solutions”, stating that “[u]sing these companies’ products can have a negative impact on a country’s political and social image”.
The deployment of centralized Internet filtering in Bahrain is certainly consistent with the recommendations of the March 2014 report. It remains to be seen whether the recommendation of implementing centralized content filtering across all the GCC countries materializes.
Discussion
The sale of Internet censorship technology to a government with a long track record of human rights violations, including repression of freedoms of expression and association, is troubling. While online censorship in Bahrain pre-dated Netsweeper’s successful bid, this timing only serves to demonstrate that the company sold its product to a country known to censor political speech and other legitimate expression. We confirm that Netsweeper technology is being used by at least one key ISP, Batelco, to filter content including critical political speech, news websites, human rights content, websites of oppositional political groups, and Shia-related content. Netsweeper’s filtering technology is enabling the Kingdom of Bahrain to further erode its already problematic human rights record.
It is notable that the export of a Canadian-produced technology that restricts the free flow of information comes as the Canadian government tries to advance cooperation with the GCC in a number of fields, including human rights. We are unaware of whether Netsweeper’s engagement with the TRA was facilitated through any trade agreements or other initiatives of the Canadian government itself. However, the presence of Canadian-made Internet filtering technology in Bahrain being used to filter political and other legitimate content in the ways we document above raises questions about Canada’s approach to balancing business opportunities with human rights in the region. It also once again underlines serious corporate social responsibility concerns regarding Netsweeper, Inc. Netsweeper Inc, not only appears to have no public-facing corporate social responsibility policies; it published, and then removed, a document that specifies how its services can be tailored specifically to filter speech protected by international human rights laws. Our latest research suggests Netsweeper continues to court contracts for national-level filtering services that clearly infringe international human rights norms and laws, even at the risk of becoming a corporate pariah.
Acknowledgements
The authors would like to thank Daniel Valls for research assistance.
Data
Supplementary technical data for this report can be found on our github located here.
1 SNMP is a protocol used by system administrators to retrieve information and metrics about a device in real time for the purpose of remote monitoring device health. A common use would be to determine how much traffic goes over a network port over time.
2 Upon reviewing the results and performing follow up scans, we determined that our original results excluded IPs that geolocated to Saudi Arabia but whose networks are actually based in Bahrain, so these are also included in our results.
3 2Connect is operating currently under the name Infonas W.L.L as the old 2Connect domain (2connect.net and 2connectbahrain.com) now forwards to infonas.com. Additionally the acceptable use policy of Infonas explicitly mentions 2connect in the limitation of liability section.