Key Findings
- On February 12, 2014, Citizen Lab published a report1 documenting how journalists at the Ethiopian Satellite Television Service (ESAT) were targeted by a governmental attacker in December 2013, with what appeared to be Hacking Team’s Remote Control System (RCS) spyware.
- This report details the events of November 5 and 10 and December 19, 2014, when the same attacker again targeted ESAT journalists based in the United States with what appear to be two updated versions of Hacking Team’s RCS spyware.
- We link the governmental attacker to Ethiopia. The attacker may be the Ethiopian Information Network Security Agency (INSA).2
- Hacking Team has a customer policy concerning the human rights implications of its products,3 and claims it investigates and may take action in response to reported cases of abuse.4 The research findings documented in this report suggest that Hacking Team may have continued to provide updated versions of its spyware to the same attacker, despite reports of use of the spyware against journalists.
Introduction
In November and December 2014, several Washington DC-based journalists with the Ethiopian Satellite Television Service (ESAT) were targeted, unsuccessfully, with what appear to be two new versions of Hacking Team’s RCS spyware.5 This report details these attempts to infect the journalists’ computers with RCS and monitor their activity.
Our research suggests the involvement of a governmental attacker that may be the Ethiopian Information Network Security Agency (INSA) . Notably, the attacker appears to be the same entity as that involved in a December 2013 attack — also incorporating RCS — against ESAT journalists based in Belgium and the US, on which Citizen Lab previously reported.6
Hacking Team (HT) is a Milan-based developer of “offensive security” technology.7 In its customer policy, Hacking Team encourages direct reporting to the company of apparent misuse of its technology.8 It further notes that it monitors news for “expressed concerns about human rights abuses by customers or potential customers,” and that when “questions [are] raised about the possible abuse of HT software in human rights cases,” it will investigate and “take appropriate action.”9
The November and December 2014 attacks against ESAT, however, call into question the effectiveness of this policy in preventing use of RCS in a manner that undermines human rights. The December 2013 attack on ESAT journalists and Citizen Lab’s research regarding that attack were reported on in the media, including on the front page of the Washington Post.10 Additionally, the Washington Post,11 Human Rights Watch,12 and the Citizen Lab13 have all contacted Hacking Team about the case.
In spite of these indications to Hacking Team that RCS was deployed against ESAT journalists in December 2013, our current research suggests that Hacking Team RCS software utilized by the attacker remained in operation and received support — at a minimum, in the form of software updates — through November 2014.
Background
Ethiopian Satellite Television Service14 is an independent satellite television, radio, and online news media outlet run by members of the Ethiopian diaspora. The service has operations in Alexandria, Virginia, as well as several other countries.15 ESAT’s broadcasts are frequently critical of the Ethiopian government. Available in Ethiopia and around the world, ESAT has been subjected to jamming from within Ethiopia several times in the past few years.16 A 2013 documentary shown on Ethiopian state media warned opposition parties against participating in ESAT programming.17
The Washington Post says this about ESAT:18
The Washington Post reports the main concern of ESAT journalists with respect to spyware:19
As we note in our previous report, the Committee to Protect Journalists (CPJ) reports that Ethiopia jails more journalists than any other African country besides Eritrea, and says that the Ethiopian government has shut down more than seventy-five media outlets since 1993.20 CPJ statistics also show that seventy-nine journalists have been forced to flee Ethiopia due to threats and intimidation over the past decade, more than any other country in the world.21
A 2013 Human Rights Watch report detailed ongoing torture at Ethiopia’s Maekelawi detention center, the first stop for arrested journalists and protests organizers. Former detainees described how they were “repeatedly slapped, kicked, punched, and beaten,” and hung from the ceiling by their wrists. Information extracted in confession has been used to obtain conviction at trial, and to compel former detainees to work with the government.22
Technical Analysis
The remainder of this report provides detailed analysis of the November and December 2014 attacks on ESAT. First, we examine the December 19, 2014 attack in which ESAT’s Managing Director was targeted with spyware. We explain the links to Hacking Team RCS and Ethiopia. Then, we compare the November and December 2014 attacks on ESAT, and conclude that the attacker’s spyware was likely updated during this period.
December 19, 2014: ESAT’s Managing Director is Targeted
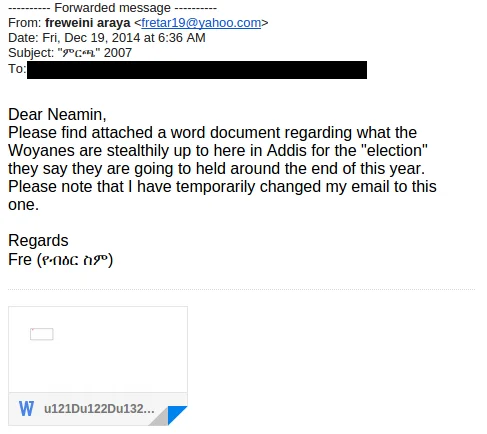
The Managing Director of ESAT, Neamin Zeleke, forwarded us the following e-mail, which he received on December 19, 2014. The e-mail contains a Microsoft Word document attachment, which he reports that he did not open:
The attached Word document (u121Du122Du132B 2007.doc) contains an exploit, which appears to be the “Tran Duy Linh” MSComctlLib.Toolbar.2 exploit:23
The exploit drops and executes the following payload:
The payload is a PE executable that appears to be protected with VMProtect, a commercial product for preventing reverse engineering and analysis of executable programs.24 The payload did not run in any of the virtual machines in which we tested it. We ran the payload on a bare metal sandbox, and observed that it attempted to communicate with the IP address 46.251.239.xxx.25
Though the contact address for the server is listed in Pakistan, a traceroute shows that it appears to be geographically located in Germany.
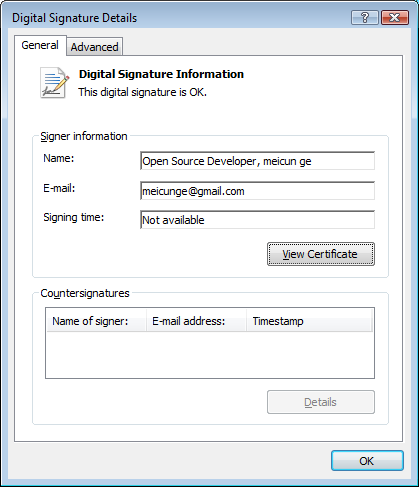
The payload is signed by the following code signing certificate:
The signature is reported as valid by Windows:
The following two samples found in VirusTotal are signed by the same certificate:
Links to Hacking Team RCS
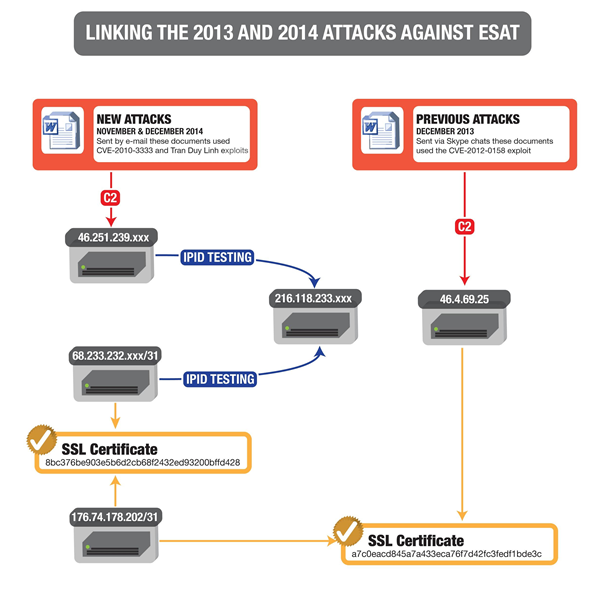
The spyware sent to ESAT on December 19, 2014, shares the same command and control infrastructure as that utilized in a December 20, 2013 attack against ESAT. The command and control server used in the 2013 attack returned an SSL certificate issued by “RCS Certification Authority” / “HT srl.”
Similar SSL certificates were returned by servers registered to Hacking Team.26 We traced the 2013 server to a broader command and control infrastructure, which includes the server used in the 2014 attacks. Below, we explain how we mapped out this infrastructure by examining SSL certificates shared between servers, and by conducting IPID testing.
In our previous work,27 we showed that Hacking Team’s clients – which, according to HT, are governments or government agencies28 — appear to use one or more fixed circuits of “proxy servers” to exfiltrate data from computers infected with RCS, through third countries, before reaching an “endpoint.”
The endpoint appeared to represent the spyware’s government operator. Leaked Hacking Team documentation refers to proxies as “anonymizers”29and data endpoints as “collectors,”30 consistent with our understanding.
Several RCS servers that we identified in our previous work use a global sequential IPID. If a server has a global sequential IPID, we can measure whether it sends packets during an interval. We sent probes to each RCS server with a global sequential IPID, and measured the value of the IPID before and after each probe. Since this test yielded consecutive IPIDs from each server, we concluded that each RCS server with a global sequential IPID was an endpoint, i.e., it was not sending the probes onward to yet another server.
We then traced proxy servers to these endpoints by sending a probe to each proxy (which each proxy forwarded to its endpoint), and inspected IPID values of each endpoint, before and after each probe, to see which one received our probe and responded to the proxy. If an endpoint received a probe we sent to a proxy, our test would show a gap in the endpoint’s IPID sequence. More details are available in our previous work.32
We used this IPID testing technique on 46.251.239.xxx, the command and control server used in the December 19, 2014 attack on ESAT. The technique showed that 46.251.239.xxx is apparently a proxy for 216.118.233.xxx, an RCS server we had previously identified.
We had previously identified 216.118.233.xxx as an RCS server, as it matched one of our server fingerprints (gleaned from servers registered to Hacking Team)33 as recently as April 7, 2014, according to Shodan.34
Most RCS servers we previously identified have now been updated so they no longer match the fingerprint.
Using our IPID testing technique, we further determined that 68.233.232.xxx/31 are also apparently proxies for the same server, 216.118.233.xxx.
The servers 68.233.232.xxx/3135 returned an SSL certificate, 8bc376be903e5b6d2cb68f2432ed93200bffd428,36 matching our fingerprint for Hacking Team RCS certificates.37
The same SSL certificate (8bc376be903e5b6d2cb68f2432ed93200bffd428) was returned38 by 176.74.178.202 and 176.74.178.203. These same servers earlier returned39 a different SSL certificate, a7c0eacd845a7a433eca76f7d42fc3fedf1bde3c, that matched our fingerprint for Hacking Team RCS certificates.
This same SSL certificate (a7c0eacd845a7a433eca76f7d42fc3fedf1bde3c) was returned40 by 46.4.69.25, the IP address of the proxy associated with the December 20, 2013 attack on ESAT, which as described in our prior report incorporated spyware that appeared to be Hacking Team RCS.41
Since the 2013 and 2014 attacks on ESAT share the same command and control infrastructure, it appears that both attacks were carried out by the same attacker(s). Figure 4 summarizes the explanation above.
Links to Ethiopian Government and INSA
The same e-mail address used in the December 19, 2014 attack on ESAT, fretar19@yahoo.com, was used on June 30, 2014, to unsuccessfully target ESAT, as well as Dr. Berhanu Nega, Associate Professor of Economics at Bucknell University.42 We could not identify the type of spyware used in the June 30 attack or find any related samples, so we do not study it further in this report. However, our analyses identified that servers at 216.118.233.25243 and 197.156.68.130 were part of its command and control infrastructure.44 The former is in the same /28 as 216.118.233.xxx, the Hacking Team RCS server we identified above. 197.156.68.130 is registered to Ethio Telecom, Ethiopia’s state-owned telecommunications company.
Since both the December 19, 2014 attack and the June 30, 2014 attack were launched from the same e-mail address, the attacker in both cases appears to be the same. Since the second attack is linked to an Ethio Telecom address, the attacker appears to be linked to Ethiopia.
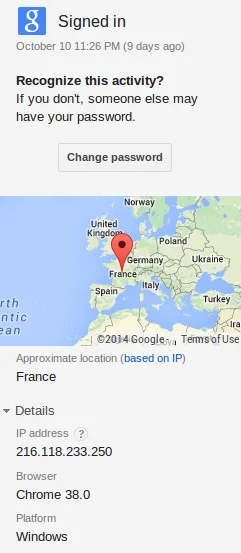
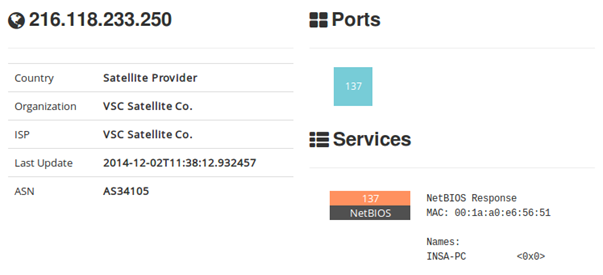
An individual not affiliated with ESAT was successfully infected by the same attacker45 in January 2014. The victim noted ongoing unauthorized access to one of his GMail accounts from 216.118.233.250,46 most recently in October 2014. The attacker may have stolen the victim’s GMail credentials with the spyware. After identifying the unauthorized accesses, the victim changed his password.
We noted that 216.118.233.250 identified itself as “INSA-PC” to Internet scanning service Shodan.47
In summary, the entity that attacked ESAT on December 19, 2014, appears to be a government, since they apparently employed Hacking Team RCS, and Hacking Team states that it provides its “software only to governments or government agencies.”48 The attacker is linked to Ethiopia via an Ethio Telecom address. The attacker also apparently controls a computer called INSA-PC, because (a) the GMail account of an individual infected by the attacker was accessed from the same IP address as INSA-PC, and (b) INSA-PC is located in between two other addresses known to be associated with this attacker. In relation to the Ethiopian Government, the acronym “INSA” refers to the Ethiopian Information Network Security Agency (INSA).49 Thus, this agency may be behind the attack on ESAT. Interestingly, INSA’s website carries a syndicated security alert about Hacking Team RCS, with tips on how to avoid being infected.50
A report by Human Rights Watch51 suggests that targeting media organizations is within the purview of INSA:
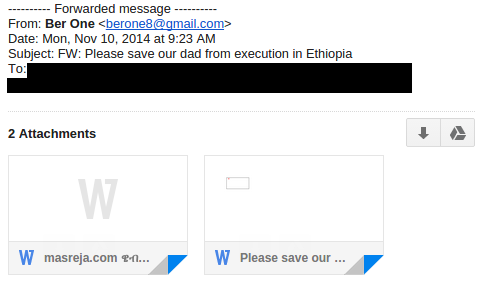
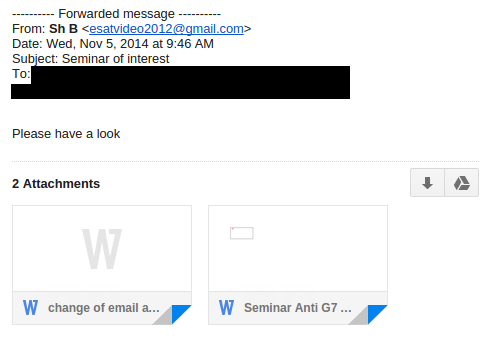
Attacks on November 5 and 10, 2014
For completeness, we report on the November 5 and 10 attacks on ESAT. ESAT journalists received the following e-mails on November 5, 2014 and November 10, 2014:
Both e-mails contain the same attachments as each other, though with different filenames. The two attachments are Microsoft Word documents with exploits. In addition to the “Tran Duy Linh” exploit apparently used in the December 19, 2014 attack, this attack also appears to make use of a CVE-2010-3333 exploit:
Both exploits drop and execute the following payload:
As in the December 19, 2014 attack, the payload is a PE executable that appears to be protected with VMProtect. We ran the payload on a bare metal sandbox, and observed that it attempted to communicate with 46.251.239.xxx, the same IP address as that involved in the December 19, 2014 attack. As described above, this IP address is linked to Hacking Team RCS, and a government attacker linked to Ethiopia.
The payload is signed by the following code signing certificate:
Evasion of Detekt as a mechanism to determine latest RCS version used by attacker
On November 19, 2014,52 security researcher Claudio Guarnieri released his Detekt53 tool, which scans a computer’s memory to check for active FinFisher and Hacking Team RCS spyware infections. Since we have samples sent to ESAT before and after that date, we examined each sample against Detekt.
Pre-Detekt RCS samples successfully detected
Detekt is able to successfully identify an infection resulting from the samples sent on November 5 and 10, 2014. The following rules, which search for humorous strings present in RCS, successfully detect this infection:
Post-Detekt RCS samples are not detected
However, Detekt fails to detect an infection resulting from the sample sent on December 19, 2014, as these strings are not present. The nonpresence of the strings is indicative of an update to the software from Hacking Team in response to Detekt. According to leaked Hacking Team RCS documentation, installation of RCS updates requires a user license file from the company.54 Moreover, Hacking Team states that without its continued support to a client, its product “soon becomes useless.”55
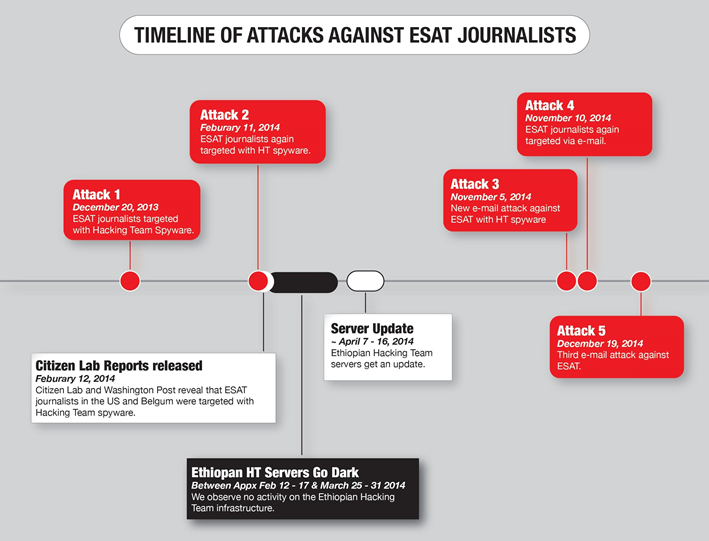
A Timeline of ESAT and Hacking Team
The latest attacks are part of an ongoing campaign against ESAT that stretches back to at least December 20, 2013. We provide a brief timeline of the attacks below:
Conclusion
Dissidents and others fleeing repressive regimes have long found a degree of protection by seeking refugee status in the West. Throughout the 20th century refugees from political persecution have established thriving diaspora communities where they have been able to continue their activity without fear of physical persecution. For at least as long, the security services from the countries they left have attempted to monitor and sometimes interfere with their activities.
We have documented a year-long campaign of spyware attacks against journalists at ESAT, using what appears to be Hacking Team’s RCS spyware. Many of the journalists targeted in these attacks are legally considered US persons, and located in the US.
In its customer policy, Hacking Team notes:
The policy suggests that Hacking Team will cease support for its technology when a client violates terms of its contract by failing to abide by applicable law. The lawfulness of government targeting of individuals based in the US with spyware, however, is in question; for example, a lawsuit brought by a US citizen against the government of Ethiopia in February 2014 claims that such actions violated the US Wiretap Act [18 U.S. Code § 2511(1)( a )].58
Hacking Team has also publicly stated that they investigate abuses reported in the press and sometimes take action:
Our 2014 report documenting the abusive use of RCS against journalists received widespread media coverage, and both the Washington Post60 and Human Rights Watch61 corresponded with Hacking Team about our findings, and received specific responses.
In the wake of our 2014 reporting, we also sent an August 2014 open letter to Hacking Team, which inquired, inter alia, about investigation by the company into the reported misuse of the software against Ethiopian journalists in the United States.62 We posed further questions about their due diligence and accountability mechanisms, while applauding their efforts to incorporate human rights considerations into their customer policy. We have yet to receive a reply to this letter.
Despite the aforementioned public reports and correspondence, this report shows that the same attacker appeared to be receiving updated versions of the RCS spyware from Hacking Team as recently as November 2014.
Citizen Lab is sending an open letter to Hacking Team, providing a copy of this report and highlighting our reasons for concern from these latest findings. Hacking Team has recently announced that it is “complying fully”63 with export controls adopted within the framework of the Wassenaar Arrangement, which includes language covering “intrusion software.”
Still, our findings suggest continued reasons for concern about the effectiveness of the mechanisms Hacking Team has in place to ensure respect for human rights in the use of their products.
Acknowledgements
Thanks to ESAT, Irene Poetranto, Adam Senft, the Electronic Frontier Foundation, and Nicholas Weaver.
Footnotes
1 Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Hacking Team and the Targeting of Ethiopian Journalists,” Citizen Lab, February 12, 2014, https://citizenlab.ca/2014/02/hacking-team-targeting-ethiopian-journalists/.
2 http://www.insa.gov.et/.
3 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy.
4 Citizen Lab, 2014, “Open Letter to Hacking Team,” https://citizenlab.ca/2014/08/open-letter-hacking-team/.
5 Hacking Team, “The Solution,” http://www.hackingteam.it/index.php/remote-control-system.
6 Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Hacking Team and the Targeting of Ethiopian Journalists,” Citizen Lab, February 12, 2014, https://citizenlab.ca/2014/02/hacking-team-targeting-ethiopian-journalists/.
7 Hacking Team, “About Us,” http://www.hackingteam.it/index.php/about-us
8 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy
9 Id.
10 Craig Timberg, “Spyware lets regimes target U.S.-based journalists,” Washington Post, February 13, 2014, http://www.washingtonpost.com/wp-srv/tablet/20140213/A01_SU_EZ_DAILY_20140213.pdf.
11 Craig Timberg, “Foreign regimes use spyware against journalists, even in U.S.,” Washington Post, February 12, 2014, http://www.washingtonpost.com/business/technology/foreign-regimes-use-spyware-against-journalists-even-in-us/2014/02/12/9501a20e-9043-11e3-84e1-27626c5ef5fb_story.html.
12 Human Rights Watch, “The Know Everything We Do – Appendix 2: Correspondance,” March 25, 2014, http://www.hrw.org/node/123976/section/12.
13 Citizen Lab, 2014, “Open Letter to Hacking Team,” https://citizenlab.ca/2014/08/open-letter-hacking-team/.
14 http://ethsat.com.
15 Id.
16 “ESAT Accuses China of Complicity in Jamming Signals,” Ethiopian Satellite Television, June 15, 2011, accessed February 13, 2014, http://ethsat.com/2011/10/08/esat-accuses-china-of-complicity-in-jamming-signals.
17 “UDJ Says Expressing Opinion to Media is Not ‘Terror’,” Ethiopian Satellite Television, January 9, 2013, accessed February 13, 2014, http://ethsat.com/2014/01/09/udj-says-expressing-opinion-to-media-is-not-terror.
18 Craig Timberg, “Foreign regimes use spyware against journalists, even in U.S.,” Washington Post, February 12, 2014, http://www.washingtonpost.com/business/technology/foreign-regimes-use-spyware-against-journalists-even-in-us/2014/02/12/9501a20e-9043-11e3-84e1-27626c5ef5fb_story.html.
19 Id.
20 “Ethiopia Arrests 2 Journalists From Independent Paper,” Committee to Protect Journalists, November 5, 2013, accessed February 13, 2014, http://www.cpj.org/2013/11/ethiopia-arrests-2-journalists-from-independent-pa.php.
21 “Ethiopia,” Human Rights Watch, accessed February 13, 2014, http://www.hrw.org/world-report/2013/country-chapters/ethiopia.
22 “They Want a Confession,” Human Rights Watch, October 17, 2013, accessed February 13, 2014, http://www.hrw.org/node/119814/section/2.
23 Malware Tracker Blog, “Tomato Garden Campaign: Part 2 – An Old “New” Exploit,” June 7, 2013, http://blog.malwaretracker.com/2013/06/tomato-garden-campaign-part-2-old-new.html. This exploit was first observed employed against “Tibet and China Democracy activists.”
24 http://vmpsoft.com/.
25 We redact the last octet of any IP address that we suspect is an active spyware server.
26 Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Hacking Team and the Targeting of Ethiopian Journalists,” Citizen Lab, February 12, 2014, https://citizenlab.ca/2014/02/hacking-team-targeting-ethiopian-journalists/.
27 Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Mapping Hacking Team’s Untraceable Spyware,” Citizen Lab, February 17, 2014, https://citizenlab.ca/2014/02/mapping-hacking-teams-untraceable-spyware/.
28 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy.
29 “Anonymizer” is defined on page x of the Hacking Team manual RCS 9: System Administrator’s Guide as “Protects the server against external attacks and permits anonymity during investigations. Transfers agent data to Collectors.” https://s3.amazonaws.com/s3.documentcloud.org/documents/1348001/rcs-9-sysadmin-final.pdf.
30 “Collector” is defined on page xi of the Hacking Team manual RCS 9: System Administrator’s Guide as “Receives data sent by agents directly or through the Anonymizer chain.” https://s3.amazonaws.com/s3.documentcloud.org/documents/1348001/rcs-9-sysadmin-final.pdf.
31 Hacking Team, “RCS 9: System Administrator’s Guide,” https://s3.amazonaws.com/s3.documentcloud.org/documents/1348001/rcs-9-sysadmin-final.pdf.
32 Page 8 of Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Mapping Hacking Team’s Untraceable Spyware,” Citizen Lab, February 17, 2014, https://citizenlab.ca/2014/02/mapping-hacking-teams-untraceable-spyware/.
33 https://github.com/citizenlab/spyware-scan/blob/master/ht/http/sonar-http/sonar-http.rb#L24-L32.
34 http://www.shodanhq.com/host/view/216.118.233.xxx.
35 This is based on data from the Sonar SSL scans, available at: https://scans.io/study/sonar.ssl; between March 31, 2014, and April 7, 2014.
36 SSL certificates in this report are identified by their SHA1 fingerprint.
37 https://github.com/citizenlab/spyware-scan/blob/master/ht/ssl/sonar-ssl/sonar-ssl.rb#L33-L47.
38 This is based on data from the Sonar SSL scans, available at: https://scans.io/study/sonar.ssl; on March 31, 2014.
39 Id. Between October 13, 2012, and February 10, 2014.
40 Id. Between October 30, 2013, and January 20, 2014.
41 Bill Marczak, Claudio Guarnieri, Morgan Marquis-Boire, and John Scott-Railton, “Hacking Team and the Targeting of Ethiopian Journalists,” Citizen Lab, February 12, 2014,https://citizenlab.ca/2014/02/hacking-team-targeting-ethiopian-journalists/.
42 http://www.bucknell.edu/x45100.xml.
43 Different from 216.118.233.xxx.
44 The spyware only attempted direct communication with 46.4.128.158 and 78.46.234.155. These two IPs returned a highly distinctive self-signed Google SSL certificate (25b734a9170e683bd05d66a7d3d8502232bb6b5f). The only other IPs in /0 that returned this certificate were 216.118.233.252 and 197.156.68.130. Thus we assume these two IPs are part of the spyware’s command and control infrastructure.
45 We judged the attacker to be the same since the infection communicated with 46.4.69.25. The infection appeared to be Hacking Team RCS.
46 Different from 216.118.233.xxx.
47 https://www.shodan.io/host/216.118.233.250.
48 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy .
49 http://www.insa.gov.et/.
50 Ethio-CERT, “Legal Spyware Works on Both Android and iOS,” http://ethiocert.insa.gov.et/web/guest/news/-/asset_publisher/nU0q/content/legal-spyware-works-on-android-and-ios.
51 Human Rights Watch, “‘They Know Everything We Do’: Telecom and Internet surveillance in Ethiopia,” March 2014, https://www.hrw.org/sites/default/files/reports/ethiopia0314_ForUpload_0.pdf.
52 https://twitter.com/botherder/status/535252116622041088
53 https://github.com/botherder/detekt.
54 Page 13 of the Hacking Team manual RCS 9: System Administrator’s Guide https://s3.amazonaws.com/s3.documentcloud.org/documents/1348001/rcs-9-sysadmin-final.pdf.
55 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy.
56 The last time Shodan recorded the servers matching our old scanning fingerprint was April 7 (http://www.shodanhq.com/host/view/216.118.233.xxx). The April 16 Sonar HTTP scan did not record the fingerprint (https://scans.io/study/sonar.http), yet the server continued to be reachable. The disappearance of this HTTP fingerprint is consistent with behavior we saw on other RCS servers.
57 Hacking Team, “Customer Policy,” http://www.hackingteam.it/index.php/customer-policy.
58 Electronic Frontier Foundation, “Kidane v. Ethiopia,” https://www.eff.org/document/complaint-32.
59 Citizen Lab, 2014, “Open Letter to Hacking Team,” https://citizenlab.ca/2014/08/open-letter-hacking-team/.
60 Craig Timberg, “Foreign regimes use spyware against journalists, even in U.S.,” Washington Post, February 12, 2014, http://www.washingtonpost.com/business/technology/foreign-regimes-use-spyware-against-journalists-even-in-us/2014/02/12/9501a20e-9043-11e3-84e1-27626c5ef5fb_story.html.
61 Human Rights Watch, “The Know Everything We Do – Appendix 2: Correspondance,” March 25, 2014, https://www.hrw.org/node/123976/section/12.
62 Citizen Lab, 2014, “Open Letter to Hacking Team,” https://citizenlab.ca/2014/08/open-letter-hacking-team/.
63 Hacking Team, “About Us,” http://www.hackingteam.com/index.php/about-us.