Citizen Lab is pleased to announce the release of “For Their Eyes Only: The Commercialization of Digital Spying.”
Read the Report [PDF]*
(updated on 16 September 2013)
The report features new findings, as well as consolidating a year of our research on the commercial market for offensive computer network intrusion capabilities developed by Western companies.
Our new findings include:
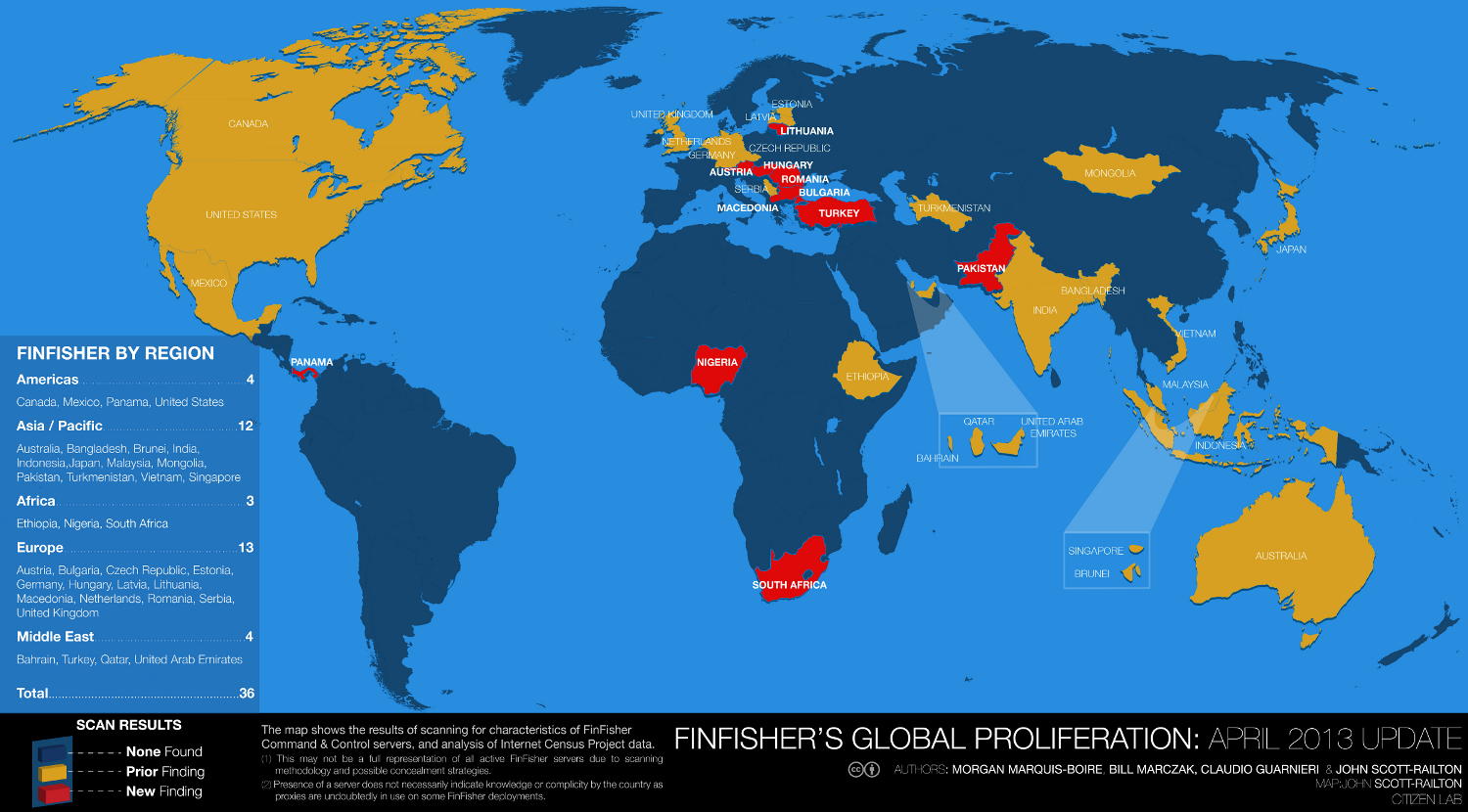
- We have identified FinFisher Command & Control servers in 11 new Countries. Hungary, Turkey, Romania, Panama, Lithuania, Macedonia, South Africa, Pakistan, Nigeria, Bulgaria, Austria.
- Taken together with our previous research, we can now assert that FinFisher Command & Control servers are currently active, or have been present, in 36 countries.
- We have also identified a FinSpy sample that appears to be specifically targeting Malay language speakers, masquerading as a document discussing Malaysia’s upcoming 2013 General Elections. Click here for a plain-language summary of our findings from Malaysia, as well as background on FinFisher.
- We identify instances where FinSpy makes use of Mozilla’s Trademark and Code. The latest Malay-language sample masquerades as Mozilla Firefox in both file properties and in manifest. This behavior is similar to samples discussed in some of our previous reports, including a demo copy of the product, and samples targeting Bahraini activists.
Our previous research uncovered evidence that FinFisher (commercial network intrusion malware) developed by UK-based company Gamma International was targeting activists in Bahrain. It analyzed mobile variants of the FinFisher suite. It also exposed the use of commercial surveillance malware developed by Italy-based company Hacking Team to target a dissident in the United Arab Emirates. Most recently, we documented the global proliferation of FinFisher command and control servers.
This research is one of the first extended projects to attempt to map out the operation and prevalence of commercial surveillance software. Our work opens a window into this space, but it remains crucial that the nature and impact of the commercial surveillance market be better understood. Technical research in this field has only just begun, but it is already clear that the stakes are high. We hope this report will contribute to discussions on this issue in technical, civil society, and policy making communities.
This research represents the joint work of Morgan Marquis-Boire, Bill Marczak, Claudio Guarnieri, and John Scott-Railton.
* Note: An early version of the report included a typographic error in a Table on page 90 that resulted in the the wrong IP address being listed for the FinFisher Server on Iusacell PCS . The error had the IP incorrectly listed as
“117.121.xxx.xxx” when it is actually “187.188.xxx.xxx”. The Citizen Lab regrets the error, which we corrected as soon as it was noticed.