The use of remote surveillance software against activists has been a feature of the ongoing conflict in Syria. In February 2012, CNN reported that “Computer spyware is the newest weapon in the Syrian conflict”. Since then numerous electronic campaigns targeting Syrian activists have been observed. These have included: a phishing campaign involving the compromise of a high profile Syrian opposition figure; malware targeting activists by claiming to be documents regarding the foundation of a Syrian revolution leadership council; and, malware purporting to be a plan to assist the city of Aleppo.
The majority of these attacks have involved the use of Dark Comet RAT. Remote Administration Tools (RAT) provide the ability to remotely survey the electronic activities of a victim by keylogging, remote desktop viewing, webcam spying, audio-eavesdropping, data exfiltration, and more.
The use of Dark Comet in this conflict has been well documented. This RAT was the toolkit used in the malware reported on by CNN and also in the campaigns using fraudulent revolutionary documents.
In addition to Dark Comet, we have seen the use of Xtreme RAT reported on by the Electronic Frontier Foundation (EFF) and F-Secure.
Today, the EFF and Citizen Lab report on the use of a new toolkit by a previously observed attacker. This actor has been circulating malware which surreptitiously installs BlackShades RAT on victims machines. This RAT is a commercial tool which advertises the following:
“BlackShades Remote Controller also provides as an efficient way of turning your machine into a surveillance/spy-device or to spy on a specific system.”
It is being distributed via the compromised Skype accounts of Syrian activists in the form of a “.pif” file purporting to be an important new video.
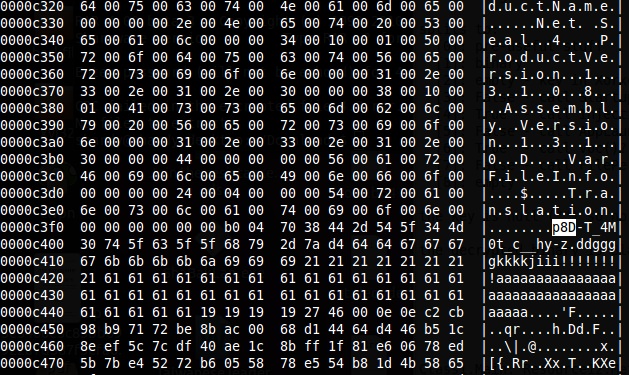
On execution the following files are dropped:
A keylogger file is then created in a the user’s temporary directory:
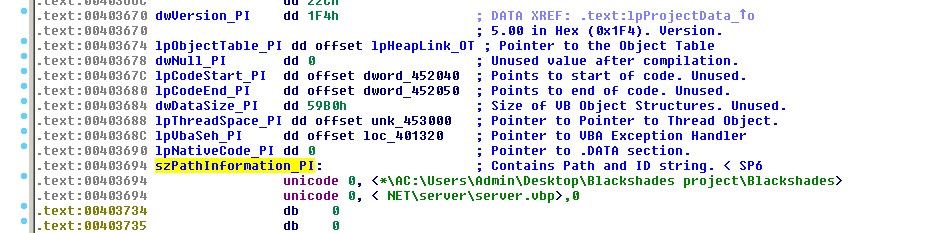
Note that ‘D3D8THK.exe’ is copy of the original file. ‘local3.exe’ appears to be a version of AppLaunch.exe, the Microsoft ClickOnce Launcher.
The following registry entries are created to allow the dropped programs through the firewall.
Note the misspelling of “Messenger” as “Messanger”.
“VSCover.exe” is added to autoruns to enable persistence.
VSCover.exe contains “Libra” (30209 bytes) as a .NET resource which is encrypted using a weak method. Decryption is possible using the key stored internally. Once decrypted, it is loaded as a .NET assembly and the Piept() function is called.1
One characteristic stands out in the Class1.Main() function: invoking an obfuscated function in a resource.
Tracing the value of Resource12.Method provides:
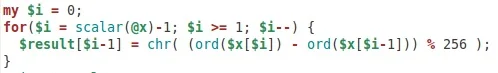
Substituting out the functions and variables, the decryption routine looks like this:
Libra has 3 classes: Mameloane2, RuntimePortableExecutable (implementing PE headers, methods for binaries to run in WinXP and Win7), and Xorxorxor (implementing decryption methods including XOR). Libra also contains the VSCover.exe program itself as an unencrypted resource.
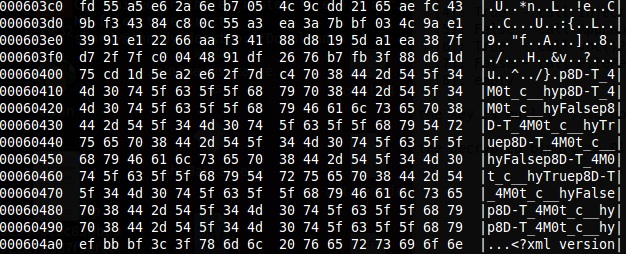
As seen above, VSCover will call the Mameloane.Piept() function in Libra. Piept() will reload the main D3D8THK program, splitting it by the string “p8D-T-4M0t_c__hy”. This string can be found in an invalid Version resource of the original binary. Looking at the code, it can be seen that the data in this resource splits out to another encrypted binary and some configuration options.
The fields extracted from the resource this way are:
The resource start and first marker string, followed by the encrypted binary data:
The configuration options (note the True and False strings):
No matter what the configuration options, Piept() will decrypt the binary, possibly using a one-byte XOR key first. In this case, the field was empty (see above at 0x60419), so the following decryption was used only:
The binary decrypts to a Visual Basic executable, which can be identified as BlackShades RAT:
This makes an outbound network connection on 4444/TCP to alosh66.myftp.org. On June 11th 2012, this had the address 31.9.170.1403.
This command and control domain is similar in naming convention to that used by the malware reported in the Guardian on March 20, 2012. In that case, a site which appeared to be a YouTube channel hosting pro-revolution videos installed malware disguised as an Adobe Flash Player update.
Instead of Adobe Flash, the malware installed Dark Comet RAT and contacted alosh66.no-ip.info.
On consecutive days in March 2012, the command and control domains for both pieces of malware pointed to the same IP address in Syrian (STE) address space:
This evidence, combined with the similar naming convention, suggest that these attacks have been performed by the same actor.
This malware package (new_new .pif) is not well detected at this time, but it is detected by some anti-virus vendors. This version of the Black Shades RAT implant (VSCover.exe), is at the time of analysis (Jun 16th 2012) undetected.
We recommend following the recommendations laid out the in the EFF blog post for detection of this malicious software and, furthermore, exercising caution when receiving executable files via Skype or other internet chat media even if they supposedly come from trusted acquaintances.
—
Footnotes:
1 piept is Romanian for “chest.”
2 Romanian for “nipples”.
3 The DNS registrar has since been contacted and the domain has been shut down.